Cyber-Ark > Privileged Identity Management 5.0

The Privileged Identity Management (PIM) Suite is a full life-cycle solution for securing, managing, automatically changing and monitoring all activities associated with Privileged Accounts.
- Secure your Privileged Accounts and administrative passwords found in routers, servers, databases, workstations and embedded in applications.
- Create a centralized point for enterprises to achieve exceptional security, streamline updates, enhance maintenance, and ensure compliance with regulations and security best practices across all types of Privileged Accounts.
The Challenge
In today's environment, organizations spend a lot of resources building an infrastructure for securing the enterprise and assuring their business continuity and compliance. Every typical IT environment comprises of hundreds or thousands of servers, databases, network devices and more, all controlled and managed by a variety of privileged and shared identities - also known as break-glass, emergency or fire IDs - which are the most powerful in any organization. This includes the Root account on UNIX/Linux, Administrator in Windows, Cisco Enable, Oracle system/sys, MSSQL SA and many more. Ironically, these identities are often neglected, difficult to monitor their session activities, and passwords are never changed. In some cases, these identities are required not only by the internal IT personnel, but also by external 3rd party vendors and, thus, require extra care, such as secure remote access and secure session initiation without exposing the credentials. Powerful passwords are also often found hard coded inside applications, scripts and parameter files, leaving them unsecured, rarely changed and visible to the world. As the "Keys to the Kingdom", mismanagement of privileged identities impose great risks to organizations:
- Audit and accountability - Compliance regulations (such as Sarbanes Oxley, PCI and Basel II) require organizations to provide accountability about who accessed shared accounts, what was done, and whether passwords are protected and updated according to policy.
- Insider threat - One of the biggest concerns today is the risk of insider threat. In many organizations, the same root or Administrator password is used across the organization, making it easier for a disgruntled insider to abruptly take down core systems.
- Loss of sensitive information - Privileged accounts usually have unlimited access to backend systems. Compromising such accounts may lead to uncontrolled access, bypassing the normal system operation. For instance, this can result in manipulating billing record and loss of money.
- Administrative Overhead - With hundreds of network devices, privileged identities can be extremely time-consuming to manually update and report on, and more prone to human error. Moreover, inaccessibility of such a password by an on-call administrator may cause hours of delay in recovering from system failure.

The Solution
The Cyber-Ark's Privileged Identity Management Suite, a full life-cycle solution for managing the most privileged accounts in the enterprise, enables organizations to secure, provision, manage, control and monitor all activities associated with all types of Privileged Identities such as administrator on a Windows server, Root on a UNIX server, Cisco Enable on a Cisco device, as well as embedded passwords found in applications and scripts. Privileged passwords, as well as the audit information associated with using them, must be protected according to the highest security standards. The Cyber-Ark PIM Suite utilizes the Patented Digital Vault®, certified as highly secure by independent security evaluators (such as ICSA Labs). This core technology is the heart of the PIM suite and was designed to meet the highest security
requirements for controlling the "keys to the kingdom". The Digital Vault provides numerous underlying security capabilities for authentication, encryption, tamper-proof audit and data protection.
The Cyber-Ark PIM Suite includes the following products:
- Enterprise Password Vault® - Cyber-Ark's award winning Enterprise Password Vault (EPV) enables organizations to secure, manage, automatically change and log all activities associated with all types of Privileged Passwords. EPV offers industry leading implementation, integration, scalability and robustness for managing hundreds of thousands of servers, databases, network devices and more.
- Application Identity Manager™ - Cyber-Ark's market leading Application Identity Manager (AIM) provides the only Application
Identity Management solution to fully address the challenges of hard-coded App2App credentials and encryption keys. The solution eliminates the need to store App2App credentials in applications, scripts or configuration files, and allows these highly-sensitive passwords to be centrally stored, audited and managed within Cyber-Ark's patented Digital Vault. - Privileged Session Manager™ - The Privileged Session Manager (PSM) enables organizations to control and monitor privileged
accesses to sensitive systems and devices. PSM provides privileged session recording with VCR-like playback, as well as secure remote access to sensitive systems using privileged single sign-on, and without divulging the used credentials to the end users.
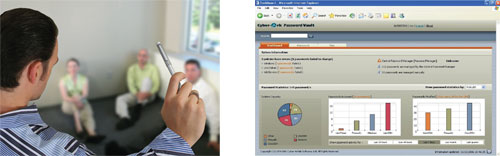
Solution Benefits
With Cyber-Ark PIM Suite, enterprises can easily:
- Manage and Protect all Privileged Accounts. Utilize a secure Digital Vault in order to store, protect, manage and control access to Privileged Accounts at a centralized point using a robust policy management engine. Cyber-Ark's patented Vaulting Technology® utilizes a fully integrated model of critical security layers, interwoven to meet the highest security needs.
- Control Access to Privileged Accounts. PIM Suite offers a simpleaccess control interface that easily pinpoints who is entitled to useprivileged accounts and initiate a privileged session, when and why.
- Initiate and Monitor Privileged Sessions. As a central control point,the PIM Suite also provides privileged single sign-on for initiatingprivileged sessions, as well as recording any activities that occurred during these sessions. PIM utilizes the Digital Vault as a tamper-proof secure storage for these session recordings.
- Manage application and service credentials. PIM provides sophisticated and transparent solutions for securing and managing critical applications as well as Application Server accounts, and eliminating the use of hard-coded and embedded passwords, making them invisible to developers and support staff.
- Comply with audit and regulatory requirements. The PIM Suite provides an easy way to create audit reports required by Sarbanes-Oxley, PCI and more. It allows enterprises to enforce corporate security policies to ensure compliance with regulatory needs and security best practices related to access and usage of privileged accounts for both human and application (unattended) access.
- Streamline management of Privileged Accounts. PIM eliminates manual administration and overhead by providing instant and automatic changing of passwords for thousands of network devices and applications, including scripts and parameter files. Its high level of automation ensures extremely reliable and uninterrupted service with minimal administrator overhead and increased productivity.
- Seamlessly integrate with enterprise systems. With an industry leading performance, scalability and robustness, PIM can protect and manage up to hundreds of thousands of passwords across a highly heterogeneous IT environment, with complex and distributed network architectures. PIM can leverage existing enterprise infrastructure and integrate with corporate core systems
- Easily set up and deploy. PIM ensures quick deployment and implementation proven in over 400 enterprise customers, providing immediate ROI by improving IT productivity.

Features
From streamlining password management to delivering the rock-solid security of a Digital Vault, the many benefits of the Privileged Identity Management Suite are powered by a robust set of system capabilities, such as:
Security and Audit
- Highly secure storage for controlling the "keys to the kingdom" utilizing FIPS 140-2 validated cryptographic module
- Centralized audit management through built-in audit-ready reports as well as self-serve access to auditors
- Sophisticated and flexible web-based access control mechanism for creating personalized views of password access
- Tamper-proof storage for critical corporate PIM-related information, such as audit records, session recordings, policies, and more
Shared and Administrative Account Management
- Out-of-the-box policy based automation and management for a heterogeneous IT environment with over 50 types of managed devices, including most operating systems, databases, firewalls, network devices, routers and more
- Extensible device-management architecture with flexibility to introduce support to additional systems and devices as needed
- Self recovery solutions such as automatic reconciliation of passwords
- Automatic provisioning of accounts based on the enterprise directory
- Customizable request workflow of privileged accounts by integrating with enterprise help desk and ticketing systems
Application Identity Management
- Multi-platform easy to use API for eliminating hard coded passwords from applications, scripts and configuration files
- Unique patent-pending solution for eliminating passwords from Application Server data sources, with no code changes and no downtime during password change
- Secure offline caching for application resiliency, performance and HA
Privileged Session Management
- VCR style playback of recorded privileged sessions
- Highly scalable solution supports multiple recording servers for LB/HA
- Secure remote HTTPS-based access for enterprise managed devices
Enterprise Readiness
- Integration with enterprise infrastructure, including LDAP and IAM integration for user management, authentication products (2-factor, RSA, Radius, PKI, LDAP and more), monitoring and SIEM integration using SNMP, Syslog and SMTP, built-in HA/DR architecture and much more
- Full Software Development Kit (SDK) to integrate with a myriad of enterprise systems
- Distributed Architecture with central management that is ideal for multi-network and multi-site environments, and benefits from central administration, audit and monitoring with full performance load-balancing of password management
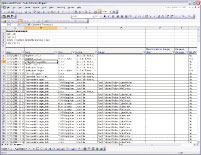
Built-In Auditing Power
The Cyber-Ark PIM Suite includes a rich set of auditing reports, such as the one pictured here. Additional audit features include the ability to track time, date, a personalized identity, changes made and logging history.
Reports are available to auditors in self-service formats or exportable to Microsoft Excel.










